.bit - the next generation of bulletproof hosting
Published on 25th September 2017, 04:50:29 UTC
To control infected computers (so called bots), cybercriminals often use domain names for hosting their botnet Command&Control infrastructure (C&C). One of the advantages for botnet operators using domain names for botnet C&C hosting is that the A record (IP address) of the domain name can easily be changed in the case when the IP address where the botnet C&C is hosted gets disconnected or shut-down (for example as a result of an abuse complaint sent to the associated hosting provider). Another advantage is the fact that the Top-level domains (TLDs) where a domain name resides in are being maintained by the Internet Corporation for Assigned Names and Numbers (ICANN) which is more or less independent from governments. While ICANN is responsible for the governance of the domain names and e.g. publishes rules for registries and registrars how to operate and manage TLDs and domain names, ICANN can't take action against domain names. However, domain names are usually an easy target for IT security researchers and law enforcement agency who may ask or force a domain registry or registrar to shut-down, seize or even sinkhole a domain name. While this is good from a perspective of an IT security researcher or policeman, it is bad for cybercriminals as they may lose the control over their entire botnet. Botnet operators where therefore looking for an alternative and pretty soon found one.
Namecoins
In 2011, yet another cryptocurrency was born: Namecoin. Namecoin is a fork of Bitcoin and uses the same code. But unlike Bitcoin, it is possible to store data with Namecoin using its own blockchain transaction database. Due to that, Namecoin can not only be used as cryptocurrency but also to create online identities (called NameID) and providing domain name registrations using its own top level domain: .bit. Unlike the usual Top-level domains (TLDs), Dot-bit is independent from ICANN and hence is not subject to the regulation and rules of ICANN. As the Dot-bit is based on Namecoin, it is completely decentralized: There is no government or organisation that can suspend or shut-down a domain name registered within the Dot-bit name space.
Another advantage of the Dot-bit name space is that domain names that are registered within .bit are completely anonymous: There is no information about the holder of a domain name (domain registrant) and hence no whois service you could query. There is no contact information, no email address and no phone number you could contact if you experience troubles with a .bit domain name.
Last but not least: Dot-bit domain names are extremely cheap. While domain names from an ICANN ruled Top-level domain usually cost between a few USD up to $ 100 and more, the price for a .bit domain is at 0.02 namecoins (NCM) which is around $ 0.024.
However, one of the problems of Dot-bit domain names is the fact the the TLD .bit is not present in the root name servers and therefore it is not possible for a computer to resolve a Dot-bit domain "out of the box". In order to resolve Dot-bit domains, the user usually has to install a special piece of software or use the alternative DNS root operated by OpenNIC in order to make the resolution of Dot-bit domain names possible.
Malware meets Dot-bit
Dot-bit and OpenNIC are wonderful alternatives to the official root DNS servers and domain name space, but they do also attract badness. While this is not a Dot-bit or OpenNIC specific problem (as all services on the internet sooner or later attract abusers), the problem with these two services / technologies is that there is no one who has control over the system and could take action against abuse. Registrars and registries who operate and sell ICANN ruled TLDs can suspend a domain name if such one is e.g. hosting a botnet C&C or child porn. Dot-bit can't do so it is based on the blockchain technology and hence decentralized:
It is therefore not surprising that botnet operators began to use Dot-bit for hosting their botnet Command&Control servers (C&C). As a matter of fact, this is not a new phenomena: Trend Micro has already published a research paper on the abuse of Bitcoin domain names in 2013. What actually is interesting is the fact for how long botnet C&C that are taking advantage of a .bit domain stay active. Unlike botnet operators who host their botnet C&C infrastructure in one of the "official" Top-Level domain names such as .com and usually get shut-down sooner or later, cybercrime operations that are using .bit do apparently have a pretty long life time.
Let's take pationare.bit as an example: The domain name has been registered within the Dot-bit name space in December 2016. It has obviously been registered by botnet operators to host Chthonic botnet C&C domain name (Chthonic is an ebanking trojan that evolved from the infamous ZeuS trojan) and is not hosting any legit content. The Chthonic campaign associated with it is using the RIG exploit kit to infect victims computers when they visit a compromised website (drive-by infection). The said RIG EK campaign has been documented in 2016 and 2017 by Brad from malware-traffic-analysis.net.
2016? You would normally say that this domain name has likely already been taken down ages ago. But this is not the case: As it is hosted within the Dot-bit name space, the domain name (and the botnet C&C that is hosted on it) are still active - after almost 9 months. I can't think of any botnet C&C domain name I've seen in the recent years that managed to stay online for such a long time. Quite bulletproof, isn't it?
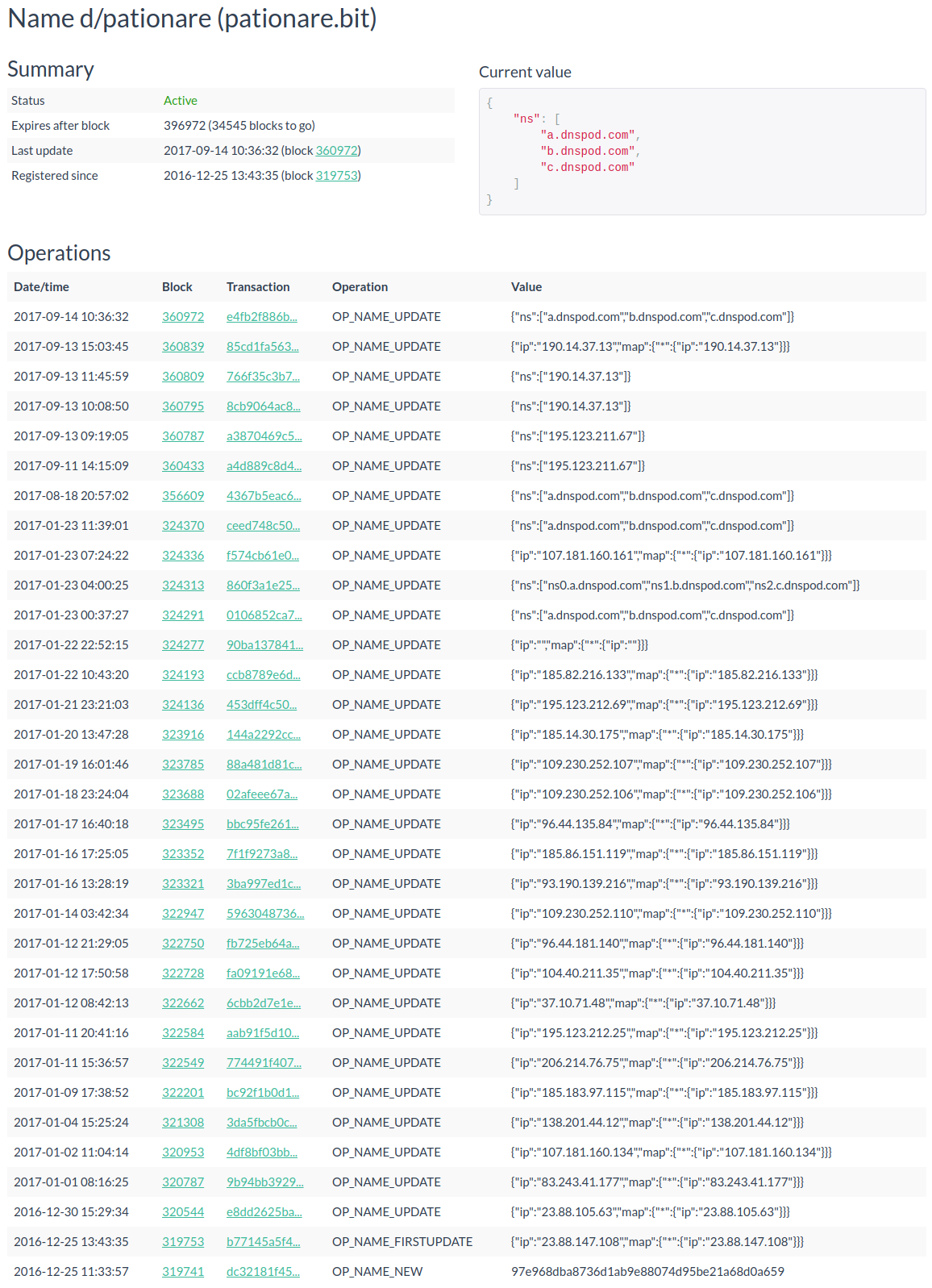
The screenshot above, which I took from namecha.in, does not only reveal the registration date of the domain name and when the blockchain has been updated but also every operation that updated the domain names record. As namecha.in reveals, the domain name has been updated several times, usually with an IP address (A record) of the botnet C&C. It also shows that the botnet operators played with the NS record and are now using an Chinese DNS provider called dnspod.com as delegated DNS server for the domain name.
While this sounds all fantastic from the perspective of a cybercriminal, they had to solve one important problem: As the TLD .bit is not in the DNS root zone, how should the malware be able to resolve it? That's where OpenNIC enters the game. In almost all of the botnet campaigns I've seen in the recent 12 months, the botnet operators use a list of DNS servers of the OpenNIC project that the cybercriminals have hardcoded in the malware:
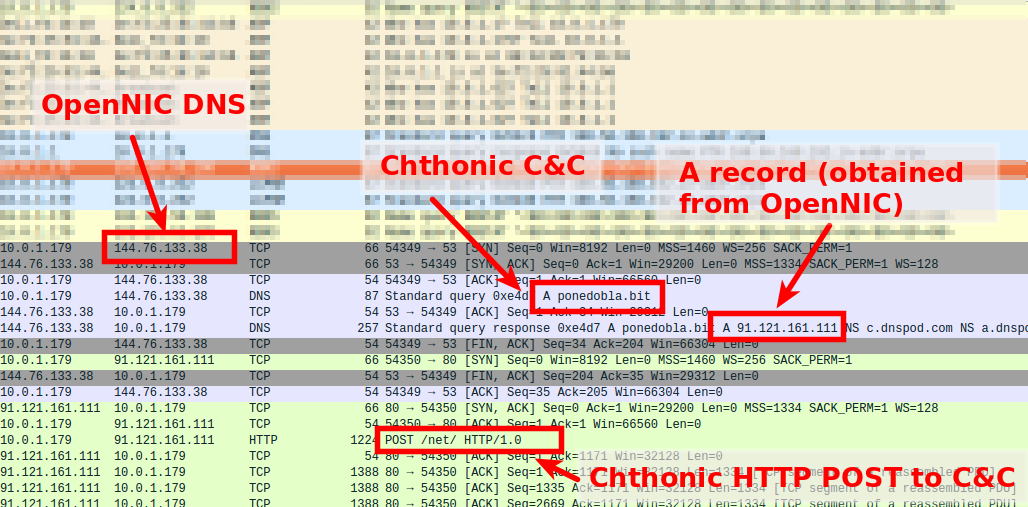
The screenshot above originates from a full network capture (pcap) I've took from a Chthonic sandbox run. It shows that the malware queries a DNS server of the OpenNIC project (in the example above this is 144.76.133.38) for the botnet C&C name ponedobla.bit. Namecoin tells the OpenNIC DNS server that it should ask dnspod.com from where it then obtains the domain name's A record (IP address) of the botnet C&C. OpenNIC returns the A record to the querying client (bot) which then sends a HTTP POST request to the C&C (that HTTP POST request is actually Chthonic beaconing to its C&C).
OpenNIC - a democratic alternative DNS root
OpenNIC promotes itself as a democratic alternative DNS root that is operated by volunteers who donate 61 public servers. Taking a look at some of the recent sandbox runs I noticed that some of the .bit botnet C&C domain names do not resolve. After some further analysis I came to the conclusion that some of the OpenNIC DNS server must do some sort of filter. I therefore decided to do some testing:
| OpenNIC servers tested: | 59 | |
|---|---|---|
| None-resolving: | 7 | |
| Online: | 52 | |
| .bit support: | 52 | |
| Servers apply blacklisting: | 8 |
It appears that, out of 52 tested OpenNIC DNS servers, 8 of them (15%) apply some sort of blacklisting:
;; QUESTION SECTION: ;pationare.bit. IN A ;; AUTHORITY SECTION: pationare.bit. 86400 IN SOA localhost. filtered.due.to.abuse. 1 604800 86400 2419200 86400
The conditions under which some of the OpenNIC DNS operators apply blacklisting is unknown. Some of the Botnet C&C domain names I've tested appear to be filtered while others aren't. While I do appreciate the effort of some of the OpenNIC DNS operators keeping abuse away from their service, I must say that it is sad that only 15% of the OpenNIC DNS servers apply blacklisting at all. Also, I think it gives the users of OpenNIC a bad user experience because, as depending on the OpenNIC DNS server you use, some (bad) domain names are either filtered or not. For the malware itself it seems that this doesn't matter as it apparently just quries the next OpenDNS server should a domain name doesn't resolve.
Conclusion
I've seen an emerging trend in the use of .bit domain names for botnet C&C hosting. Not only Chthonic is using Dot-bit for hosting its Command&Control infrastructure but also other malware families such as Smoke Loader (Dofoil), Backdoor.Teamviewer, Necurs, Shifu or TinyNuke.
I do hope that the operators of OpenNIC will apply some comprehensive blocking of botnet C&C domain names in the near future. If you or your organisiation is not using OpenNIC, I would recommend you to block the OpenNIC DNS servers for the moment (e.g. on the firewall). This will prevent that an infected computer, such as the Chthonic campaign mentioned above, is able to reach its botnet Comannd&Control server (C&C) and receive commands / tasks from the botnet herder as well as drop stolen information from the victims computer (such as login credentials, credit card information, etc).
Ressources:
Further reading: